Thank you! Your submission has been received!

White Paper
Introduction
When a person intrudes on a property, a security team may first locate and then apprehend the trespasser. With drones, this response becomes three-dimensional. Technology can alert security to the presence of an intruding drone, and technology can eliminate the intrusion. With smart airspace security in place, security providers can look beyond the immediate yet illegal instinct to eliminate the threat by force and instead turn to existing standard operating procedures (SOP’s) to advance their response protocols before, during, and after a drone incursion.
Stage 1: Before the Incursion
Smart drone detection technology automatically alerts security providers when an unauthorized drone enters protected airspace. Sensors capture information about the aerial intruders, including the type of drone, flightpath, and location.But how should security teams react when an unauthorized drone enters protected airspace? For organizations beginning their airspace security program, key to the success of their counter-drone technology is creating proactive response protocols in the event of a drone incursion.
Stage 2: During the Incursion

Stage 3: After the Incursion

As technologists, we are consistently talking about product features. While having the most comprehensive anti-drone solutions is vital, the technology is only as good as the security teams who use them. A philosophy of develop, test & enhance is essential for security teams and must be considered adjacent to the technology investment. The consequences of drone incursions can be costly, from operational downtime to physical property damage and even data breach. With early detection and in-depth data, security teams can protect operational continuity, prevent losses, and regain control of their airspace.
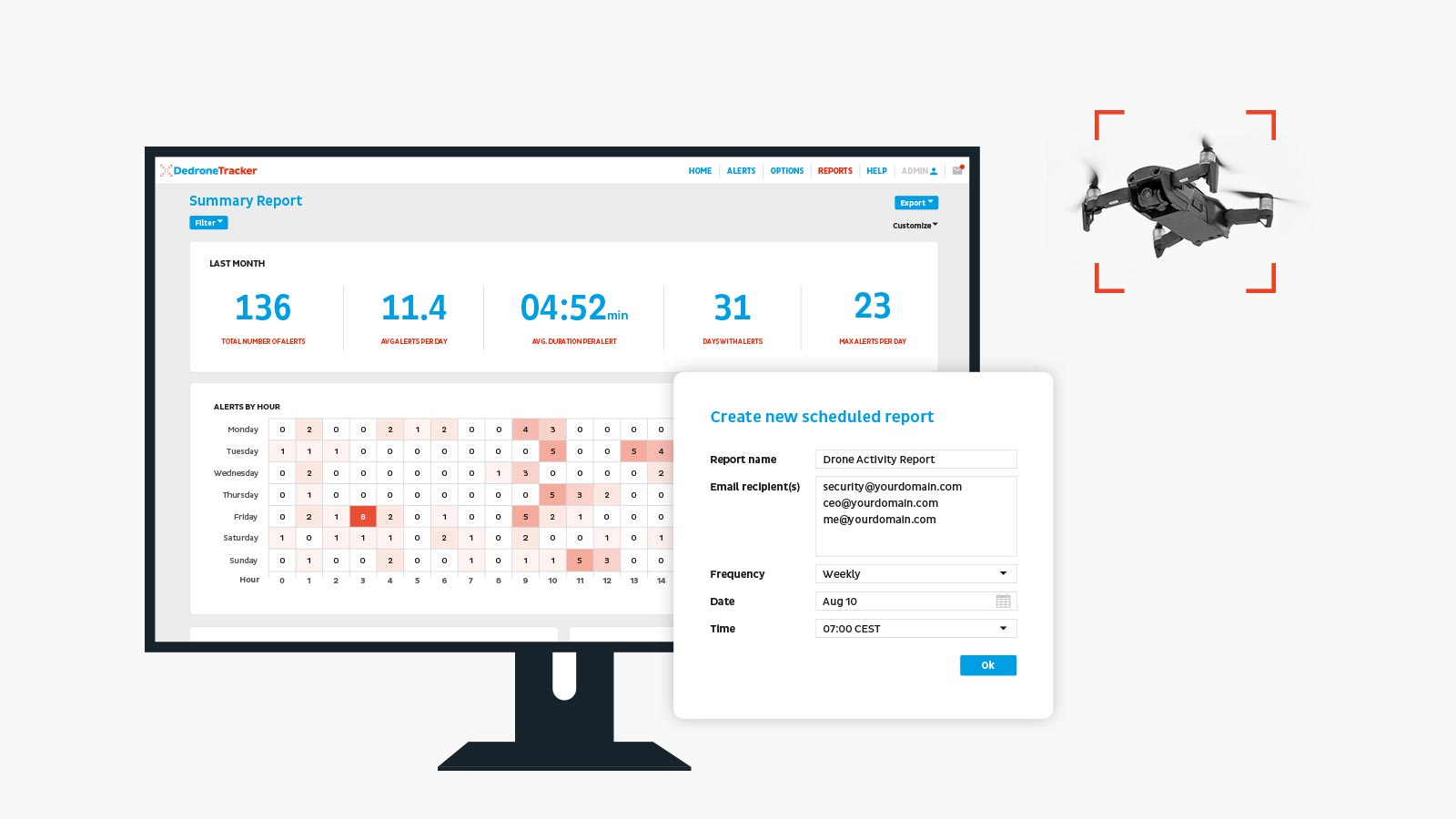
Data Driven SOPs
Airspace activity data must first be collected an analyzed in order to build a threat profile and to strategically implement SOPs. This data....RF sensors, cameras and radar. Sensor information is then analyzed from the AI/ML driven DedroneTracker.AI. Analytics can be accessed via DedroneTracker.AI or fed into Command and Control (C2) systems.
With smart airspace security data, security teams can then leverage information to develop data-driven SOPs for every stage of the drone incursion. Uncover Patterns in Drone Activity:
Conclusion
Start today by assessing the true nature of drone activity over your site. With early detection and in depth data, security teams can protect operational continuity, prevent losses, and regain control of their airspace. As more drone regulations go into effect, supporting the productive use of drones in our society the increasing the use and number of drones in our airspace, law enforcement will play a larger role. In February 2021, a drone pilot was caught flying in restricted airspace over the Super Bowl and was charged by the U.S. Department of Justice with violating national defense airspace. If convicted, the drone pilot will face a maximum penalty of one year in federal prison.